If you own or use a wireless router, you probably know about the security issues surrounding the use of a wireless network. In it’s most basic sense, the router transmits an Internet connection wirelessly to any device that can receive the signal within a proper range. That means, with an open network, anyone can connect to your router and use your Internet connection if they have a wireless card and are in range. That means external people can use up your bandwidth, AND, they may carry out malicious activity on your account. There are various security features to help keep routers protected. If you don’t care too much about the security of your data (as in packets being sent over the network), but you do want your wireless signal to be restricted, then I have an easy solution. It’s called MAC Address filtering (also called the Access List on my router).
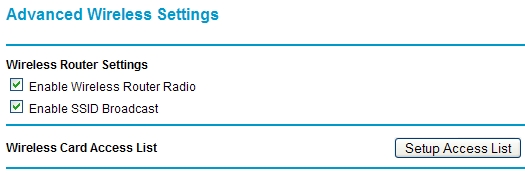
Get your MAC Addresses
The first thing you need to do it collect your MAC Addresses from all of the computers you want to ALLOW on the network. In Windows, open a command windows and enter the command ipconfig /all. You may also follow a previous tip I wrote about and enter cmd /k ipconfig /all into the Run box. Scan through the output for the line “Physical Address“. Write down the number/letter sequence on that line and keep track of them all. The Physical address is another name for a MAC (Media Access Control) address, because the MAC is unique for each piece of hardware and burned into it.
Create your “Access List”
Now it’s time to put the list together. Each router is different. My Netgear calls MAC filtering the “Access List.” Find your version of the access list and enter your respective MAC addresses into the list.
What it does and doesn’t do
This method is intended to keep only the people you trust connected to your router. There is no encryption with this method. Any person not on the list will not be able to connect to the network.
This method does not include encryption, so any packets that are sent over a network can be sniffed. This means anyone outside the network can use a packet sniffer to try to see what you’re doing. This probably won’t happen, but I’m just wanring you that this method does not involve any encryption.
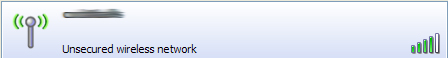
As you can see, the network is considered “Unsecured” since there is no encryption. To anyone, it looks like they’ve found free Internet access, but when they try to connect, they will get a message saying they are unable to connect.
A good idea. However, I think that any ‘malicious’ person could simply find out the MAC of a client on the network. Then spoof their own MAC to be the same as the client’s MAC. Then they could connect to you’re network as if there was no protection at all. If you knew what you were doing, you could probably gain access in a few minutes.
I’d recommend a nice and long WPA key to keep people like myself out.